Encrypting Data to Prevent Data Leaks Caused by a Stolen or Disposed Machine
By encrypting data on the machine's memory, you can prevent possible data leaks when you replace or dispose of the machine, or even if the machine were to be stolen.
Encrypting data on the memory
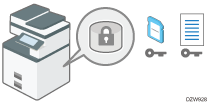
Encryption is an effective measure against data leaks. Be sure to keep the encryption key secure to use for decryption. Print it on a sheet or save it to an SD card.
Overwriting data to prevent restoration
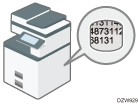
You can delete data that you do not want to be restored. The Erase All Memory function deletes all data and initializes the memory of the machine.
Encrypting Data on the Memory
![]()
- Keep SD cards and USB flash memory devices out of reach of children. If a child accidentally swallows an SD card or USB flash memory device, consult a doctor immediately.
You can encrypt data contained in the Address Book, authentication information, and stored documents to prevent data leaks in case the memory is removed from the machine.
Once encryption is enabled, all data subsequently stored on the machine will be encrypted.
The encryption algorithm used in the machine is AES-256.
![]()
The machine cannot be operated while encrypting data, updating the encryption key, or canceling encryption.
Do not turn off the power of the machine while encrypting data, updating the encryption key, or canceling encryption. If you turn off the power, the memory may be damaged and all data may be unusable.
The encryption process takes several minutes. Once the encryption process starts, it cannot be stopped.
The encryption key is required for data recovery or migration to another machine. Be sure to keep the encryption key secure by printing it on a sheet or storing it in an SD card.
To transfer data from the machine to another machine, you must decrypt the encrypted data. Contact your service representative for data migration.
If you specify both the Erase All Memory function and the encryption function, the Erase All Memory function is performed first. Encryption starts after the Erase All Memory function has been completed and the machine has been rebooted.
![]() Log in to the machine as the administrator on the control panel.
Log in to the machine as the administrator on the control panel.
![]() On the Home screen, press [Settings].
On the Home screen, press [Settings].
![]() On the Settings screen, press [System Settings].
On the Settings screen, press [System Settings].
![]() Press [Settings for Administrator]
Press [Settings for Administrator] [File Management]
[File Management]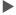 [Machine Data Encryption Settings].
[Machine Data Encryption Settings].
![]() Press [Encrypt].
Press [Encrypt].
If the data has been encrypted, you can decrypt the data or back up the data.
Cancel Encryption: Cancels encryption.
Back Up Encryption Key: Makes a backup of the encryption key. The encryption setting is not changed. Proceed to Step 7.
![]() Select the location to store the encryption key.
Select the location to store the encryption key.
Save to SD Card: Saves the encryption key to an SD card. Insert an SD card into the media slot, and then press [Save to SD Card]
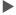 [OK].
[OK].
Print on Paper: Prints the encryption key on a sheet of paper. Press [Print on Paper]
 [Print].
[Print].
![]() Press [OK].
Press [OK].
![]() When the confirmation dialog is displayed, press [Exit].
When the confirmation dialog is displayed, press [Exit].
![]() Press [Home] (
Press [Home] ( ), and then log out of the machine.
), and then log out of the machine.
![]() Turn off the main power of the machine, and then turn it back on.
Turn off the main power of the machine, and then turn it back on.
When the main power is turned on, the machine starts to convert the data on the memory. Wait until the message "Memory conversion complete. Turn the main power switch off." appears. After that, turn off the main power again.
Initializing the Machine with the Erase All Memory Function
Overwrite and erase all data stored on the memory when you relocate or dispose of the machine. The device settings stored on the machine's memory are initialized.
For details about using the machine after executing Erase All Memory, contact your service representative.
![]()
If the method of Random Numbers is selected and overwrite three times is set, the Erase All Memory process takes up to 45 minutes. You cannot operate the machine during overwriting.
![]() Log in to the machine as the administrator on the control panel.
Log in to the machine as the administrator on the control panel.
![]() On the Home screen, press [Settings].
On the Home screen, press [Settings].
![]() On the Settings screen, press [System Settings].
On the Settings screen, press [System Settings].

![]() Press [Settings for Administrator]
Press [Settings for Administrator] [Data Management]
[Data Management] [Erase All Memory].
[Erase All Memory].
![]() From the list next to Erase Method, select an erase method.
From the list next to Erase Method, select an erase method.
The default erase method is [Random Numbers], and the default number of overwrites is [3].
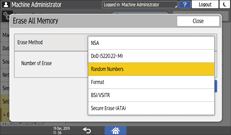
NSA*1: Overwrites data twice with random numbers and once with zeros.
DoD (5220.22-M)*2: Overwrites data with a random number, then with its complement, then with another random number, and the data is verified.
Random Numbers: Overwrites data multiple times with random numbers. Select the number of overwrites from one to nine.
Format: Formats the memory. Data is not overwritten.
BSI/VSITR: Overwrites data seven times with the fixed value (for example: 0x00).
Secure Erase (ATA): Overwrites data using an algorithm that is built in to the memory.
*1 National Security Agency (U.S.A)
*2 Department of Defense (U.S.A)
![]() Press [Erase].
Press [Erase].
![]() Press [Yes].
Press [Yes].
![]() When the Erase All Memory process is completed, press [Exit], and then turn off the main power of the machine.
When the Erase All Memory process is completed, press [Exit], and then turn off the main power of the machine.
![]()
Initialize the settings on the control panel as necessary. Press [System Settings]
 [Settings for Administrator]
[Settings for Administrator] [Data Management]
[Data Management] [Restore Default Control Panel Settings] to initialize the data, including the individual application settings and cache memory.
[Restore Default Control Panel Settings] to initialize the data, including the individual application settings and cache memory.
